Key government security initiatives making slower than anticipated progress
The Government Accountability Office released two reports, completed in March and released publicly on Monday, that highlight slower-than-expected progress being made on key government-wide information security initiatives. The first report focuses on the Federal Desktop Core Configuration (FDCC) program, which mandates minimum security baselines for client computers in federal agencies running Windows operating systems (so far it covers XP and Vista). The program is managed by the National Institute of Standards and Technology, who publishes the secure configuration specifications (akin to DISA security technical implementation guides but somewhat less robust and covering fewer types of systems) and produced the XML-based security content automation protocol (SCAP) to facilitate the process of validating secure configuration settings using automated scanning tools. FDCC compliance has been required for federal agencies since February 1, 2008, with agencies obligated to test and validate appropriate security settings for computers in their environments as part of the continuous monitoring required under FISMA. The GAO report notes that as of last September, none of the 24 major executive agencies had adopted the required FDCC settings on all applicable workstations, and 6 of the 24 had yet to acquire a tool capable of monitoring configurations using SCAP. In the aggregate, it appears that agencies do not consider deviations from FDCC configuration settings to be a source of significant security risk, as many agencies that reported such deviations also indicated they had no plans to mitigate them. For its part, GAO’s recommendations for FDCC seem largely focused on improving agency education and support for implement FDCC monitoring and achieving compliance. The report also included agency-specific recommendations for 22 of 24 agencies.
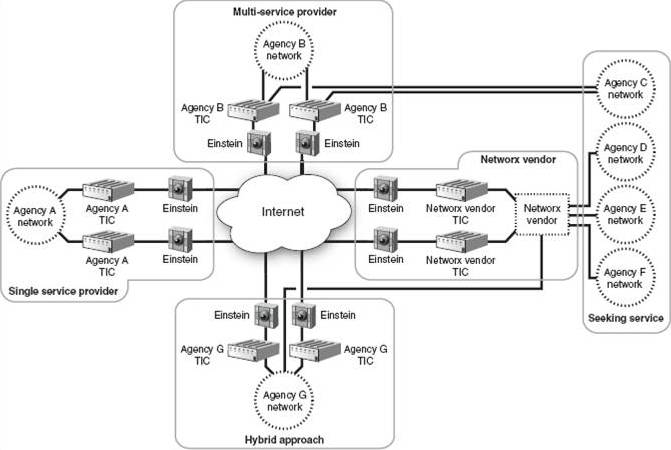
The second report addresses progress to date on the government’s initiative to secure agency connections to the Internet under the Trusted Internet Connections (TIC) program, which was announced in late 2007. Under TIC, agencies were instructed to drastically reduce the number of connections of their networks to the Internet, with an overall program goal of reducing total government Internet connections to 100 or fewer. Agencies were required, as part of their IT infrastructure planning, to propose a target number of Internet connections (and the locations of those connections) to OMB by the end of June 2008. As an interim milestone, under TIC agencies were supposed to reduce the total number of existing Internet connections to approximately 1,500 by then end of the 2009 fiscal year, but GAO found that overall the government was running about 15% short of that goal, and of the 19 agencies reporting the status of their connection consolidation efforts, none had reached an 80-100% level of progress, and just about every agency still has far more Internet connections than they “should” based on the plans of action they produced more than 18 months ago. While it’s possible that the overall targets and timeline for the TIC initiative were overly ambitious or unrealistic, there remains a sense of urgency regarding TIC because of its relation to one of the key national critical infrastructure protection programs, the Department of Homeland Security’s Einstein intrusion monitoring system, which itself is in pilot phase with aggressive plans for widescale roll-out. The Einstein program predates the TIC by several years, but the practical implementation of comprehensive government network traffic monitoring is something only made feasible if the number of sites being monitored is reduced to a manageable number. 
The vision for Einstein (as shown in the graphic above, which appears in the GAO report) includes placing intrusion detection sensors at every TIC-approved point of connection to the Internet, although in practice the number of monitoring sites may be less than suggested by TIC connection counts if DHS succeeds in deploying the Einstein system within the environments of major network service providers to the government.
 SecurityArchitecture.com
SecurityArchitecture.com
