Installing a Syslog Server
Sending Snort output to the screen or to standard log files is fine for testing purposes, to be able to monitor and analyze alerts and other output Snort produces typically requires additional processing and presentation. One way to facilitate monitoring Snort output is to direct it to a system log (syslog) server so that an analyst can monitor Snort activity using a syslog viewer. Syslog is a common component in many Unix and Linux environments, but is not typically found on Windows, as these operating systems tend to rely on built-in Windows event, system, and security logs. Several syslog servers are available to run on Windows, including several free products. The key steps for setting up a syslog server are the same for most basic syslog products: install the syslog server, configure it to listen for syslog event traffic, and start the server so that it receives Snort output.
Before installing a syslog server, you need to download an installer package. There are many options available, including several free or open-source projects such as the Syslog Server available for download from Sourceforge at http://sourceforge.net/projects/syslog-server/. This particular syslog server is quite old, so if you are doing more than basic experimentation you might be better off with a more current project such as WinSyslog (available at https://www.winsyslog.com/download/). The instructions below refer to the Syslog Server tool, but most others work in a very similar manner.
- Install the syslog server by launching the executable installer file: SyslogServer-1.2.3-win32.exe.
- When the installer completes, start the server by double-clicking on the appropriate desktop icon or choosing the server from the Windows start menu.
- To run syslog on the same computer as Snort, there should be no further configuration required for the syslog server.
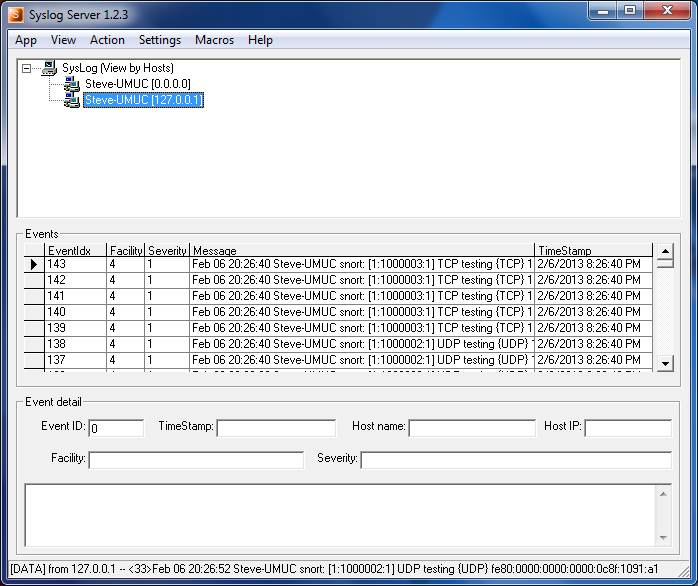
Syslog is a relatively simple protocol. It uses UDP to send messages from any program or system that generates syslog output to the syslog server. By default syslog uses port 514 (on Linux or Windows platforms). In real-world deployments, the syslog server typically runs on a different computer than the programs sending output to it, but in the current scenario both Snort and syslog run on the same host. The syslog server default address is therefore 127.0.0.1, the localhost address. The address and port are not strictly required in this situation, but for clarity we will include them in snort.conf.
- To get Snort to direct output to the syslog server, open the snort.conf file and edit the output plugin configuration for syslog, so it reads: output alert_syslog: host=127.0.0.1:514, LOG_AUTH LOG_ALERT
- Save the snort.conf file
- Open a command shell by locating Command Prompt in the Accessories of the Windows start menu
- Right-click on Command Prompt and select “Run as administrator”
- Navigate to the directory where Snort is installed: c:\Windows\system32> cd \Snort\bin
- Start Snort: c:\Snort\bin> snort -i 2 -c c:\Snort\etc\snort.conf -s
- Follow the testing procedures described in Generating Alerts to trigger the testing rules for icmp, tcp, or udp
The -s option in the Snort startup command directs output to syslog, using the settings in the snort.conf file. Without outputting to screen, no activity will appear in the command shell window where Snort is running, but as alerts occur they will appear in the syslog viewer, as illustrated in the screenshot below (showing Syslog Server). Note that until Snort or some other program on the system is generating syslog output, there may not be a host listed for 127.0.0.1. It is recommended that you start the syslog server first, then start Snort.
 SecurityArchitecture.com
SecurityArchitecture.com