Installing Snort on Linux
There are many sources of guidance on installing and configuring Snort, including several instruction sets posted on the Documents page of the Snort website. These and other sets of online instructions often note some of the pros and cons for installing from source versus installing from packages, but many only provide detailed guidance for installing from packages. This is certainly a viable option, and there are many valid reasons (and frequently encountered frustrations when compiling from source) that provide arguments in favor of package-based installation. One of the most compelling arguments against installing from packages, however, is that on most Linux distributions it is unlikely that available packages represent the latest version of the software you are trying to install. With respect to Snort, which undergoes several updates each year, this can present a limitation for anyone looking to utilize the latest features in Snort or to ensure that the most current rulesets can be used. It is still possible to work in isolation with an earlier version of the software, and for basic introductory purposes there are not too many technical gaps to constrain learning about the way Snort works. The following set of instructions assumes you have decided to install the latest version of Snort and compile from source.
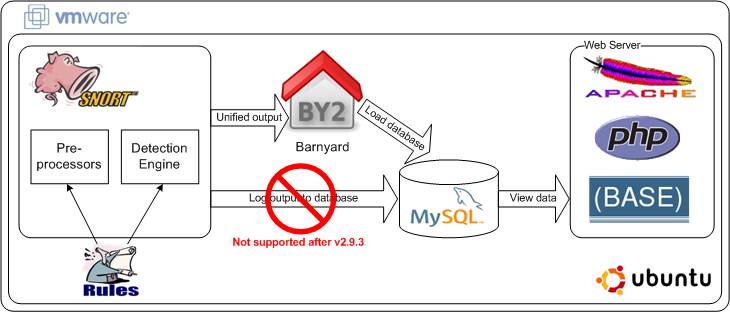
Creating a fully functional Snort environment that reflects a real-world production implementation of the IDS involves installing and configuring quite a few separate tools, as indicated in the logical diagram below. Within Snort there are a large number of available preprocessors and rules of different types that may be useful in different environments depending on what is running in those environments, what information assets need protection, and the kinds of user behavior or business processes that are expected to occur. Receiving and analyzing network traffic in Snort is often the central focus, but it is just one piece of the technical puzzle. The second major function is handling the alerts and other types of output generated by the IDS. The most common alternatives for handling Snort output include sending it to a standard logging utility such as syslog, writing the log output to the screen or a monitoring console, or generating output in Snort’s special unified2 format and processing it with Barnyard. For our purposes we’ll assume that the goal is to get alert data into a database for further inspection and analysis, so we will have Snort produce unified2 output and use Barnyard2 to load that output in a MySQL database. The primary benefit of using Barnyard instead of direct database logging is speed – spooling unified2 output to a file for processing by Barnyard is less processor-intensive than maintaining a live database connection and inserting event records in the database – so in production environments where IDS processing capacity is a priority, it is a good idea to off-load output handling to a tool like Barnyard. Note: the Sourcefire project responsible for Snort development and enhancement deprecated direct output logging to databases beginning with v2.9.3, so there is no longer a database output plugin in the tool. Once Snort output is in the database, the next step is to make the alert data available for visualization and analysis, in this case using BASE (an application primarily written in PHP) to provide summary and detail level information about alerts generated by Snort or any other tool that might have the capability and permissions to write to the tables in the MySQL database.
You can use the following instructions with your own local Linux instance (if you have one or want to set one up), or create a virtual Linux instance instead to run on another platform, such as Windows or Mac OS X. If you want to use your own, skip to “Getting and Installing Necessary Tools”; if you want to use a virtual machine instance of Linux, go to “Using VMware to Create a Linux Environment”. You can also jump directly to any part of the instruction set by using the links in the list of steps below.
Snort Installation Steps
- Creating a Linux Virtual Machine
- Getting and Installing Necessary Tools
- Retrieving Source Files
- Installing Tools from Source
- Setting Up MySQL to Work with Snort
- Configuring Snort
- Compiling Shared Object Rules
- Setting up Barnyard2
- Generating Alerts
- Prerequisites to Installing Base
- Installing BASE
- Enabling Graphing in BASE
 SecurityArchitecture.com
SecurityArchitecture.com